1.Encryption is easy to use. See below to download applications and view tutorials and links.
2.Encryption, a process that scrambles communications, allows only those with the decryption key to read one's messages. An encrypted message looks like random alphanumeric gibberish to the human eye.
The longer the key, the more time and computer power it requires to decrypt, or unscramble, the message.
3.Not all encryption is equal. Encryption from a centralized provider such as Apple or Google could be decrypted upon demand. End-to-end encryption (E2EE) prevents of third-parties from accessing data as it travels from sender to receiver. Types of encryption depend on how they are generated and shared:
a.Symmetric encryption uses a single secret key. Both sender and recipient have the same key, and can encrypt and decrypt all messages with it.
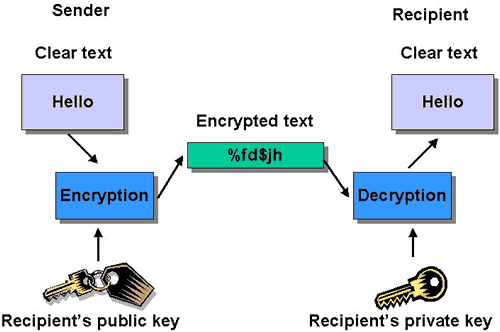
b.Asymmetric or public key encryption uses a "key pair," two related keys, one public and one private. The public key is available to everyone. A sender needs to know the recipient's public key to encrypt a message for him/her/them. Only the recipient will have the private key. The private "secret" key decrypts messages encrypted with the public key.
4.Pretty Good Privacy (PGP) is an example of end-to-end encryption for email. It uses a combination of hashing, data compression, symmetric-key cryptography, and public-key cryptography, and is extremely secure. You can only use it to encrypt messages to other PGP users. You can download PGP at the International PGP homepage by selecting GnuPG for your operating system. To learn more about how to use PGP, the Electronic Frontier Foundation has some clear articles here:
5.OTR, Wickr, iMessage or Signal are end-to-end encryption systems for instant messaging; Tresorit, MEGA or SpiderOak for cloud storage; ZRTP or FaceTime for telephony; and TETRA for radio. Signal app is free and works on the iPhone and on Android. Signal enables encrypted text messaging and private voice calls with other Signal users, and without SMS and MMS fees. Signal will also handle unencrypted communications so you don't have to switch back and forth between apps.
6. Tor is a free anonymity tool that hides your Internet Protocol (IP) address, and thus masks your identity. The Tor Bundle is an extremely easy to use browser that allows you to use the web without being tracked. Tor does not encrypt your communications. Unencrypted communications will still be readable once they exit the Tor network.
7.Some U.S. and other government officials have been pressuring companies and the public to agree to weaken encryption with backdoors, or strategically placed weaknesses in order to ensure access to encrypted communications. Backdoors make communications systems less secure. As Apple CEO, Tim Cook put it: "If you put a key under the mat for the cops, a burglar can find it too."
8.Terrorists use encryption. But there is no evidence that intelligence in Paris failed because of encryption. Intelligence has to be smarter and more diverse in its use of technology.
9.Everyone, not just government officials and elites, should have equal access to secure end-to-end encryption technology. Public education about encryption is an intrinsic good: The more the public uses encryption, the greater security and privacy it can enjoy. Many constituencies depend on encryption: students, journalists, human rights workers, individual inventors and companies.
10.A public that can communicate securely and without government interference experiences greater freedom of speech, deeper dissemination of knowledge, more authentic communication and wider communal cooperation. In an increasingly global digital world, encryption protects democracy.
For an encryption glossary, click here.
For a YouTube tutorial series, click here.
For The NSA page, click here.
For James Comey, Director of the US Federal Bureau of Investigation, speech about cybersecurity, click here.