"The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized."
Breaking News: The Honor System Does Not Work
Remember the September day when the DOJ "stopped" construction of the Dakota Access Pipeline on Federal Lands, but asked for a "voluntary pause" on construction on private lands? DAPL has ignored that request from the DOJ and is likely actively working with Morton County authorities to invade the cellular network and personal information of peaceful protestors on sovereign land. Mass arrests have been a diversion from secret completion of the pipeline.
In fact the DOJ request to voluntarily stop construction on private land has been met with a project that is almost completed, just waiting for President Obama to give the final OK. A ban on drones in the airspace was lifted yesterday, and this is the resulting footage. Obama's suggestion yesterday that everyone just "wait it out" has been received as a slap in the face by Water Protectors.
The First Amendment is already under attack. Just ask Amy Goodman of Democracy Now!, who had a warrant issued for her arrest because she was reporting from the DAPL construction site. They came for Goodman, now they are coming for everyone else, with no regard for the Fourth Amendment.
Now, it appears that DAPL and Morton County have not only trashed the Fourth Amendment, but they may have their pipeline as a result.
Spying on the Water Protectors
Is Fourth Amendment protection against illegal search and seizure under attack at the Standing Rock Sioux Reservation? Apparently more than water protectors, allies, and journalists who are on site at the junction of the Cannonball and Missouri Rivers share the suspicion that cellphones are monitored.
On October 20, the National Lawyers Guild (NLG) and the American Civil Liberties Union (ACLU) submitted FOIA and Open Records Requests to investigate the possible use of unconstitutional surveillance at Standing Rock. In a press release the NLG and ACLU noted the obvious, that "Water Protectors and allies have been continuously surveilled by low-flying planes, helicopters, and drones, and have had local cell phone communications jammed and possibly recorded."
The organizations submitted Freedom of Information Act (FOIA) and North Dakota Open Records Act requests to multiple state and federal agencies in response to the surveillance and arrests of those attempting to stop construction of the Dakota Access Pipeline (DAPL).
An investigator from the Federal Communications Commission has subsequently interviewed John Wathen, a photojournalist whose photos accompany this article.
"The FCC has opened an investigation into the use of "Stingray" technology against Water Protectors. If true, this is a serious issue to be dealt with especially over sovereign land," Wathen said.
It would certainly explain how Morton County authorities were always one step ahead of any prayer service or gathering before they made mass arrests.
The FCC investigator was not available for comment.
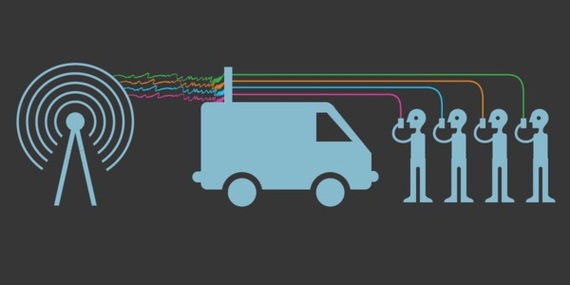
So, what is Stingray technology and why would the FCC be interested in its deployment?
Stingrays are called IMSI catchers, because they catch the "international mobile subscriber identity" of cell phones. Go to your smart phone keypad and type in *#06# and a number will display on your screen. This is your unique IMSI number and it can tell Stingray your identity by disclosing the person paying for your carrier service; most likely you. In the hands of law enforcement, this means that you are essentially being searched without a warrant and law enforcement can get away with it because there is no paper trail to prove it is being deployed. In passive mode, Stingray listens, and in active mode your phone can be accessed. Passive mode is enough cause for alarm, since your voice communications, texts and pretty much anything on your phone can be captured, along with your location. This is all done without a warrant for probable cause.
So, how does Stingray work?
"Stingray" is the brand name for an IMSI catcher. It functions as a fake cell-phone tower, small enough to fit in a van, a plane, or even a backpack. If your phone comes between the Stingray and the closest cellphone tower, it tricks your phone into thinking the Stingray is an actual tower. This fake tower intercepts all communication. It is likely that many residents of Morton County North Dakota who travel along ND Highway1806 and have nothing to do with the actions at Oceti Sakowin camp have also been monitored and had their personal information compromised. This should be food for thought for residents of the county who have been strangely silent on the illegal actions of their Sheriff.
The signs and symptoms of Stingray intrusion have been affecting cellphones.
This writer has had my cellphone overheat when I was not using it. My battery mysteriously drained and I was constantly returning to my car to recharge. Signals would spike and then disappear. This did not mean I was specifically targeted, but it does indicate that my phone was encountering a fake tower.
I was not the only one. Cellphone disruption on a wide scale, unmarked vans plying the back roads, and the constant presence of fixed wing aircraft and helicopters over the camps have been troubling. Complaints prompted the NLG and ACLU of North Dakota to request all surveillance information and communications regarding the DAPL protests from April 1 to the present from federal and local agencies.
But the bad news is that it will be a quixotic quest.
To get a warrant, the government must show there is probable cause. The only way a judge can make this decision is for the government to tell the truth about what it is doing. Since there is no paper trail for search and seizure with Stingray use, why bother with a judge?
In "FCC Helped Create the Stingray Problem, Now it Needs to Fix It," the Electronic Frontier Foundation (EFF) addresses the over reach of law enforcement in other police actions.
We now know, for example, that police departments use them for hours at a time without a warrant, that officers deploy them for tracking down people suspected of non-violent crimes like harassing phone calls, and that certain devices do in fact cause significant interference to cell service. The combination of the extraordinary power of these surveillance tools (they can scan hundreds of innocent user cell phones at once) and the lack of FCC regulations has resulted in explosive growth in their deployment.
The government has been absolutely secretive about this technology. EFF notes that the FBI "withholds documents in FOIA requests, failing to explain (or even understand) the technology to a Texas federal judge and in Rigmaiden, misleading the court about the fact it's even using one at all."
Daniel Rigmaiden is the man who first discovered Stingray. Facing charges of tax fraud he believed he was living totally off the grid while filing tax returns for the deceased. Stingray technology caught him because of the cellular AirCard he used to access the Internet. Ringmaiden spent his time in prison researching how he was caught and fighting the illegal search and seizure. No one doubts that he should be in prison, but should he be there as a direct result of Fourth Amendment violations? It is a cautionary tale.
Minnesota Senator Al Franken, along with eleven other Senators, sent a letter to the FCC in early October.
We are particularly concerned about allegations that cell site simulators--commonly referred to as "Stingrays"--disrupt cellular service and may interfere with calls for emergency assistance, and that the manner in which cell site simulators are used may disproportionately impact communities of color. While we appreciate law enforcement's need to locate and track dangerous suspects, the use of Stingray devices should not come at the expense of innocent Americans' privacy and safety.
The Franken Letter notes that the use of Stingray devices violates Section 333 of the Communications Act, specifically "the willful interference with a communications network." Also, local law enforcement agencies do not have the "requisite licenses to operate Stingray devices over the wireless spectrum--licenses required by Section 301 of the Communications Act."
The Franken Letter also notes the disproportionate use of electronic surveillance in "communities of color."
Senator Franken's office offered this response when asked about the possible use of Stingray technology at Standing Rock
As a member of the Senate Indian Affairs Committee, Senator Franken has worked closely with Minnesota's tribes for many years, and has long pushed to address the many injustices inflicted on the native population in our country. The Senator strongly supports the right to peacefully protest construction of the project, and he is monitoring the situation in North Dakota very closely.
So what are the odds that FOIA requests will be successful?
The redactions in recent documents released by the FBI under FOIA requests would be laughable if this were not such a serious issue.
In another instance, in 2015 the FBI released more than 5,000 pages of documents regarding its internal handbook. Nearly all of it is redacted, except for correspondence between the FBI and manufacturers of the Stingray hardware.
Another Fait Accompli
Water Protectors, journalists and supporters of the Great Sioux Nation should be aware and perhaps leave their phones at home, in their cars, or put them in airplane mode while at the camps.
It turns out that it really does not matter that the Department of Justice recently required that all federal law enforcement agencies--and all state and local agencies working with the federal government--are required to obtain a search warrant supported by probable cause before they are allowed to use Stingray technology.
The vague "special circumstances" wording is not helpful and can give carte blanche to law enforcement and DAPL interests.
Water protestors report that DAPL crews are working day and night and guards are posted on the bluffs and hills.
The the Digital Smoke Signal's drone today showed what has been happening.
The honor system does not work. Remember what happened when sacred burial grounds were destroyed when DAPL interests obtained court documents showing the exact locations of graves?
Now they likely know the exact location of anyone with a cell phone.
If all this is not bad enough, listen to this update from Indigenous leader Winona LaDuke.