When hackers stole 250,000 passwords from Twitter, some if not all of those victims could become a target for identity theft. In the growing complexity of identity theft schemes, villains are relying on several tactics to gain access to your protected data on the Internet. You can protect yourself by employing a simple plan to outsmart the underlining schemes that the identity thieves rely on to steal your identity.
Some may feel this concept is a given, but identity thieves steal identities to profit -- the person stealing the identity might not be the person using it -- but they can sell the information on the Internet's black market.
This article is going to focus on the concept of how a hacker stealing passwords from a single website could lead to identity theft and a unique solution to protect your personal information online. But before we get too far, we should quickly discuss some of the advanced tactics identity thieves use to steal your identity.
One of the most common covert schemes used to steal your identity is to exploit your online trusted relationships. If you're an avid user of email or social media -- you may have seen this phishing attack before: You receive an email or message from a trusted friend saying "Hey I would like your input on this, can you check this link out www.google.com" (www.google.com is just an example, but in the real scheme the link is to a website that contains malware). Unfortunately what really happens in this scenario is a malicious actor compromising your friend's email/social media account and sending messages on their behalf. This activity could be automated on their end by creating a virus called a worm, which will spread from computer to computer, mobile phone to mobile phone and/or mobile phone to computer similar to the common flu. If you are not immune to the particular strain of flu, you will likely get it -- same is true with a worm -- if you click the link -- you have a high probability of infecting your digital device.
The malware that we are finding installed on systems ranges from a key logger that will record your every keystroke, a botnet which could make your system apart of a larger group of computers used to distribute malware and attack other systems or even spyware that is designed to send information about your computer/mobile device back to the malware owner.
Some identity thieves will purchase your usernames and passwords that were hacked from a website. While the purchase itself could be considered trivial, the hack to grain access to a websites usernames and passwords may have been very advanced.
If you're a contemporary web user, you might have recently seen options on your favorite websites to "login to this website from your Facebook account" or "login to this website from Twitter account" to authenticate. Users choose do this because it's easy -- you login to Facebook, like millions of other users everyday, and then click the "login via Facebook" so you don't need to remember another username and password. Sounds good right? Well -- this example is just simplifying "using the same password for multiple websites" which is a high risk if you're concerned about identity theft.
If a hacker compromises 250,000 Twitter passwords, and you're one of the users who were victimized and used the same password for multiple websites including your email account -- you might be in some serious trouble.
For example -- most people use an online banking system in some form or another. Some banks even allow you to make deposits by taking pictures of the front and back of the check with their smartphone app. But in order to have an online banking account, you need to have an email account. You also need an email account to setup Twitter. And we all use different passwords for our online accounts, right?
Let's pretend you're a smart web user and use different passwords for Twitter and your bank. However, you used the same password that you used for Twitter that you use for your email - and Twitter's website gets hacked and your password is exposed. Now, all someone needs to gain access to your bank account is to initiate a password reset. From there they can do just about anything that you can do from your account like report a debit card lost/stolen, initiate a funds transfer etc.
Here are some modern recommendations that could help prevent identity theft:
Use two factor authentication if available. When you log into a website, you typically use a username and password combination -- which is also what hackers can steal from websites. What if you needed your cell phone as well -- something you physically have in your possession? Using two factor, when you login to a website with your username and password, a text message is sent to your phone and you need to input the content of the text message to the website. This method goes above and beyond something you know, but adds the element of something you have (your mobile phone). Google does this and I recommend everyone to start using it now -- even if a hacker infects your computer with a key logger, they wont have your cell phone and can't access your account.
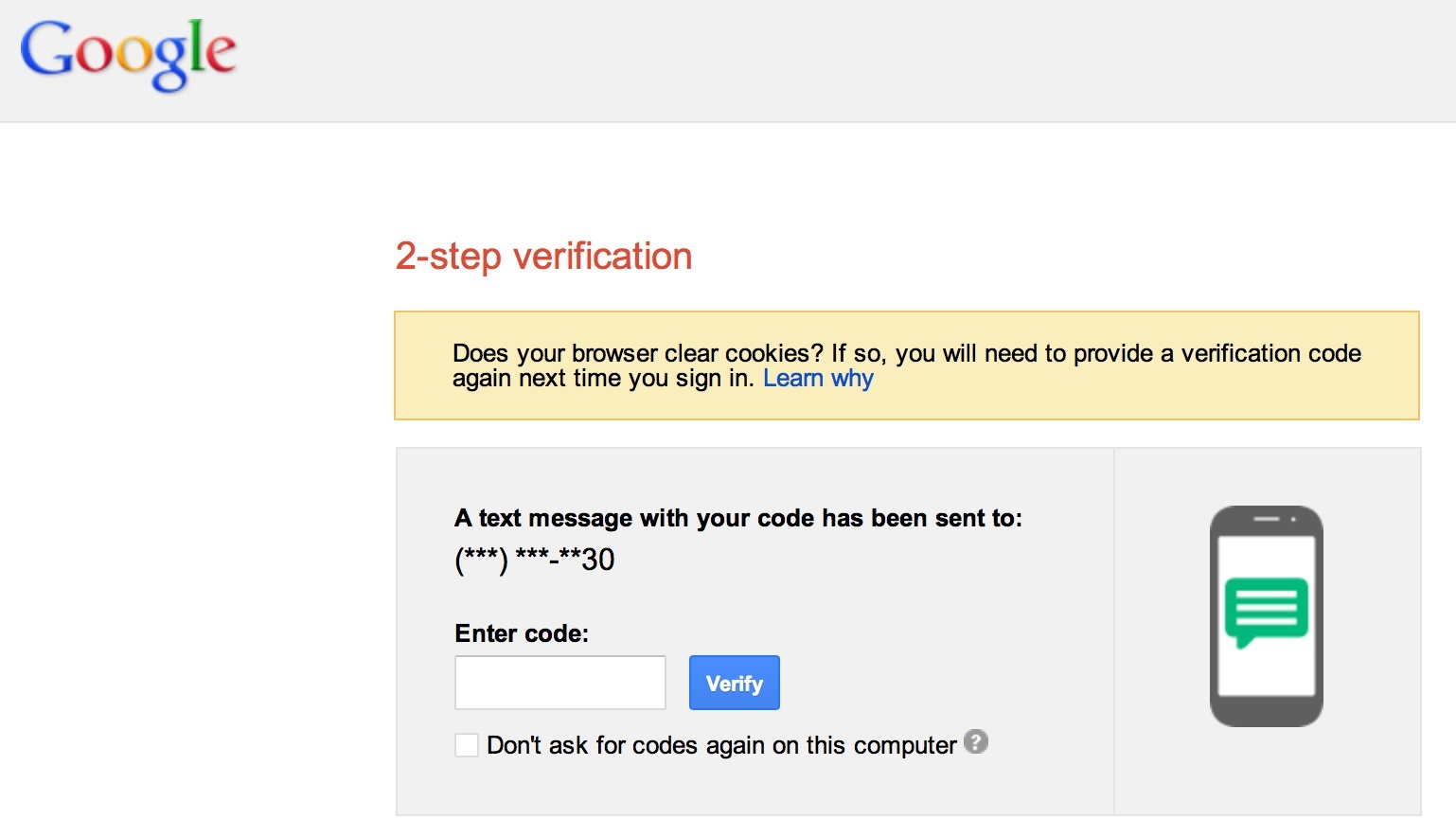 After you present your username and password, Gmail will challenge the user to present the contents of a text message (Google can also call you and dictate the code over the phone).
After you present your username and password, Gmail will challenge the user to present the contents of a text message (Google can also call you and dictate the code over the phone).
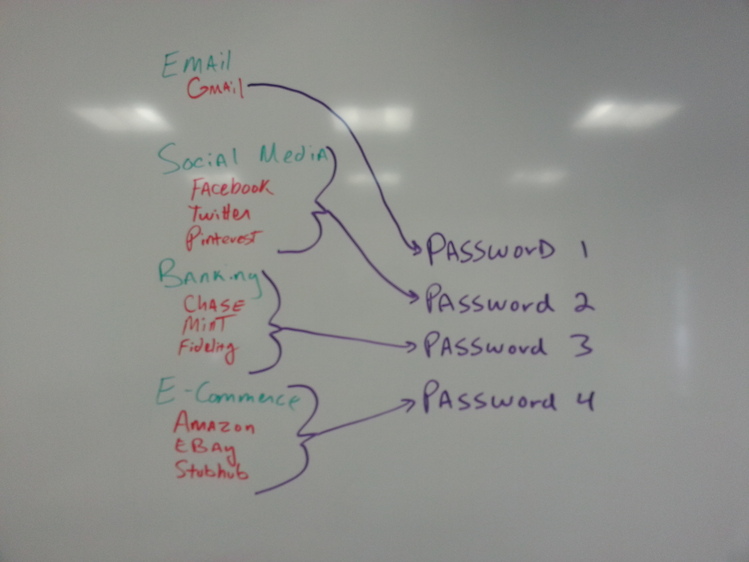
Compartmentalize your passwords. Some experts will recommend unique passwords for every website -- which is good advice, but practically hard to accomplish. As an alternative, you could group your web activity into several "buckets" and design a password scheme including a passphrase so it's easy to remember.
- Social Media - Password variation 1
- E-Commerce - Password variation 2
- Banking - Password variation 3
- Email - Password variation 4
For example -- if you use Facebook, Twitter and Pinterest -- you can use the same "strong" password for all three services. If one of those websites becomes compromised, your Amazon, eBay, Gmail and bank accounts are still safe.
So back to the concept of a passphrase -- "Open Sesame" is one that we've all heard in some form or another, but it's a good example of using a passphrase. "Open Says a Me" grouped together creates an 11-character password (minus the spaces). You could complicate and strengthen the passphrase by adding the following "Open!Says@mE2013" now you have 16 character alpha/numeric/symbol based password which could lower the probability of it being easily broken.
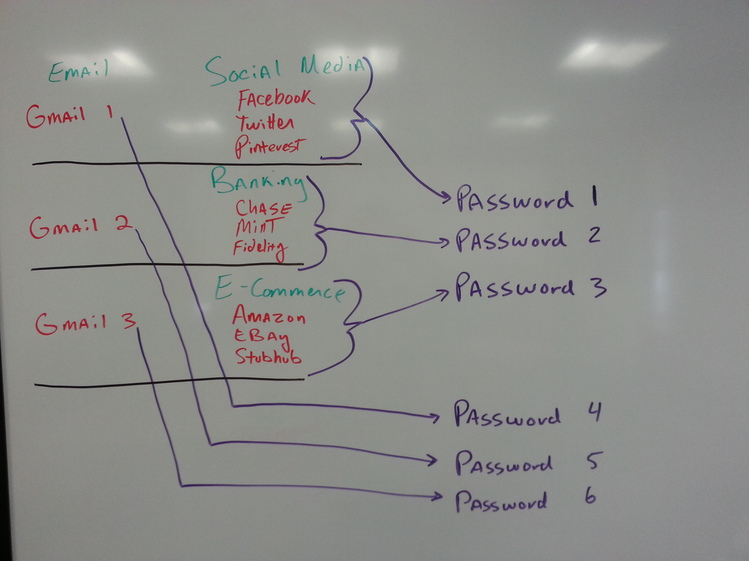
By using password compartmentalization -- if an attacker discovers one set of passwords, they can't get access to all of your information. The flip side of not compartmentalizing passwords is if your Twitter account credentials get compromised, then everything you have access to could as well. You could also strengthen your compartmentalization by using additional email accounts for each group. This does add a layer of complexity but also potentially burdensome in that you will need to access multiple email accounts to see all of your emails.
There is no silver bullet to stop identity theft -- but hopefully you can use some of the above advice to improve the odds of you not becoming victimized.
Some questions for readers:
What tactics to you use to avoid becoming victim of identity theft?
Have you ever been a victim of identity theft? What was your experience like trying to recovery your identity?