UPDATE: Twitter has published a blog on the "OnMouseOver incident," explaining what happened, why, and how Twitter responded.--UPDATE: Twitter announced on its Status blog that it had addressed the vulnerability:
We’ve identified and are patching a XSS attack; as always, please message @safety if you have info regarding such an exploit. We expect the patch to be fully rolled out shortly and will update again when it is.
At 6:50AM PT, Twitter wrote, "The exploit is fully patched."
Does it seem to be resolved as far as you can tell?
--Twitterers should watch out for a security flaw on Twitter that can automatically redirect users to third-party sites and launch pop-ups--even without users clicking on the spurious links.
Initially dubbed the Twitter "mouseover bug"--just hovering your mouse over an infected link can launch pop-ups, third-party sites, and for some even send tweets--the exploit, which uses the OnMouseOver Javascript command, seems only to be affecting users on Twitter.com. Users are advised to stay off the site and use third-party applications until it is resolved. TweetDeck, one third-party Twitter client, noted, "Affected tweets show up in TweetDeck as containing code/script. Just ignore/delete such tweets & do not view on twitter.com until fixed."
There are also reports that the new version of Twitter, unveiled last week, is not affected.
Business ETC offers one explanation of how the glitch started spreading:
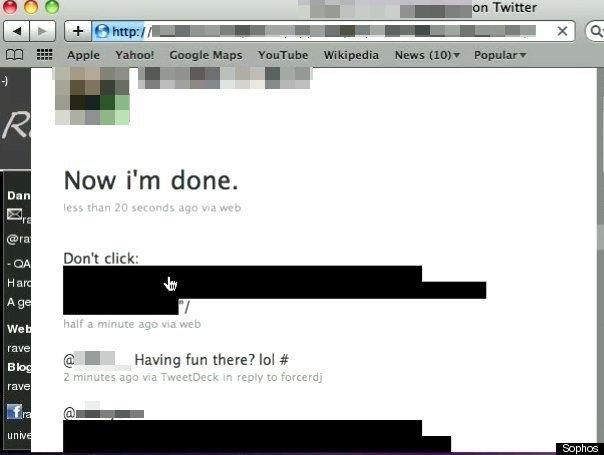
[U]sers began seeing large chunks of blacked-out text in timelines, which - when hovered over by users mistaking the message for blacked-out formatting - automatically filled the 'New Tweet' space on the page and tried to post the message.
The code in question is a JavaScript exploit which masquerades itself as a traditional hyperlink, so as to evade Twitter's automatic filters, but triggers a sequence that automatically posts the same message to a user's own timeline, thus continuing its spread.
Graham Cloley noted on his Sophos blog, "It looks like many users are currently using the flaw for fun and games, but there is obviously the potential for cybercriminals to redirect users to third-party websites containing malicious code, or for spam advertising pop-ups to be displayed."
Mashable estimates that the security flaw "has been widely exploited on thousands of Twitter accounts." Cloley observed that Sarah Brown, the wife of the former British Prime Minister, was affected. @MikeCane tweeted, "This thing is spreading so fast that Search Twitter cannot update fast enough." Another user, @Mikeful, wrote, "Seems like Twitter onmouseover-exploit is spreading like wildfire. Search page tells "14000 new tweets" after waiting 10 seconds." Because the exploit seems able to "fill and submit a status update form 'on your behalf,'" TechCrunch reports the onMouseover exploit may have spread to as many as 40,000 tweets in just 10 minutes. (Have you seen it? How has it affected you? Let us know below)
The screenshot below (via Sophos) offers a glimpse at the blacked out tweets that are to be treated with caution.
The security flaw comes at an awkward time for Twitter: the microblogging service only recently unveiled a major redesign of its website (see screenshots and features), and now users are being told to stay off Twitter.com.