The mystery of the encrypted message found in the chimney some 70 years after it had been dispatched is intriguing many, including this writer. The 27 five-letter group message comprises a message less than the size of one Twitter tweet (see below for content sizing). And as we are all becoming educated, One-Time-Pad (OTP) encrypted messages are designed, by their very nature, to be unbreakable. The security of the encryption lays with there being only two sets of OTP keypads, one for the originator (a transmit pad) and one for the recipient (an identical pad identified as the corresponding receive pad), separate OTP keypads would have been used for return send/receive transmissions so as to avoid the fatal reuse of key text.
According to an article in The Telegraph by Hannah Furness, "Wanted for one last mission: Bletchley Park codebreakers to crack the D-Day pigeon cipher"
"...it is believed to have been dispatched by British forces during the D-Day invasion to relay secret messages back across the Channel, after a radio blackout left them reliant on homing pigeons.
The Royal Pigeon Racing Association believe the bird probably either got lost, disorientated in bad weather, or was simply exhausted after its trip across the Channel.
Due to Winston Churchill's radio blackout, homing pigeons were taken on the D-Day invasion and released by Allied Forces to inform military Generals back on English soil how the operation was going.
Speaking earlier this month, Mr Martin said: "It's a real mystery and I cannot wait for the secret message to be decoded. It really is unbelieveable."
It is thought that the bird was destined for the top secret Bletchley Park, which was just 80 miles from Mr Martin's home.
The message was sent to XO2 at 16:45. The destination X02 was believed to be Bomber Command, while the sender's signature at the bottom of the message read Serjeant W Stot."
I did a little research on the timeline of D-Day. It stands to reason the good Serjeant W Stot was using GMT as the time of record, as was protocol then and now for government transmissions. The date is believed to be June 6, 1944. The message was created at 1522 GMT and transmitted via pigeon at 1525 GMT. Locale time would have been one hour later.
This time and date correspond very closely to the time of the German army's counterattack which occurred at 1620 (4:20PM CET). Three German Panzer groups engaged the allies just north of the city of Caen, coming up against the forces of the British Shropshire Light Infantry. The British and Canadian forces had not been able to link up between landing beaches Sword and Juno beaches; in fact, one Panzer group exploited this gap and drove right down to the coast. Perhaps this brief 27 five-letter group message pertained to this German counterattack.
But what if...
But what if this message holds a more cryptic and exotic message? Perhaps this Serjeant W. Stot was assigned to a one of the many Jedburgh teams which had parachuted in behind enemy lines on the eve of D-Day in support of Operation Overload? These teams were supported by another group carrying the identification of X2 -- that which supported the Office of Strategic Service's counterintelligence efforts. During World War II the headquarters of the OSS X2 was located in the Grosvenor Square area of London. If so, perhaps it was confirmation of a "certain item" having been captured, perhaps the Enigma encryption machine being used by the German Army? We'll probably never know for sure, as OTP by its very nature is unbreakable. But who knows? So let's take a look at the message itself:
AOAKN HVPKD FNFJW YIDDC
RQXSR DJHFP GOVFN MIAPX
PABUZ WYYNP CMPNW HJRZH
NLXKG MEMKK ONOIB AKEEQ
WAOTA RBQRH DJOFM TPZEH
LKXGH RGGHT JRZCQ FNKTQ
KLDTS FQIRW AOAKN 27 1525/6
The first and last groups are the pad control group -- AOAKN designates which OTP is being used for encoding the message, while the second group of the message HVPKD is the key control group, i.e. where the recipient should begin to decrypt the message (just in case the message arrives out of sequence -- doubt they expected a 70-year delay). The message itself begins with the third group and ends with the 26th group, 24 groups in all comprise the text. All in all, the message content is 120 characters in length, less than a modern day Tweet.
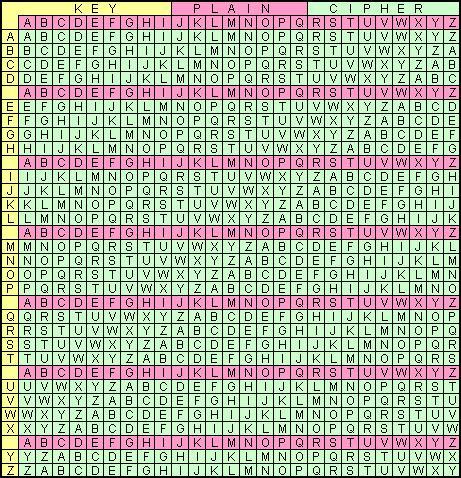
The five-letter groups were encrypted using the Vignere Table or chart, which shows how any combination of two letters results in a third, encrypted letter. Without the all important key pad, the message held in these 120 characters will be kept a secret. Which is precisely why, a well executed key distribution and management system ensures the One-Time-Pad is the most secure of all encryption systems.
Enjoy this piece of historical mission. If they find the keypad AOAKN in the historic archives or locate the good Serjeant W Stot, then the odds are increased considerably, absent such, this message will forever be kept, as it was designed -- SECRET.