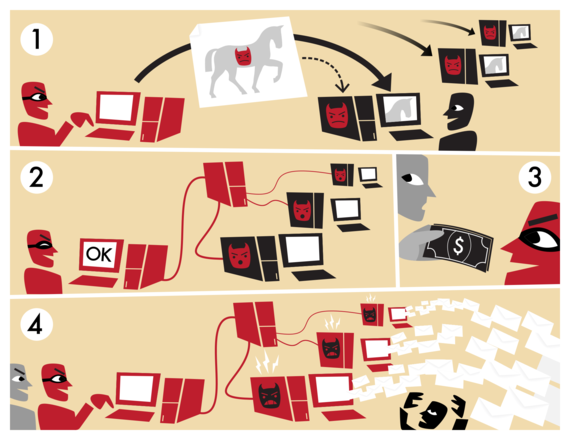
After the recent attempt upon a petition for a second EU referendum on the official website of the UK Parliament, a lot of thought has been given to the concept of chain hacking and botnets, and how it affects the security of all that is around us. With above 3.5 million signatures accumulated over the days, there is no doubt that a large number of those signatures are fraudulent, with about 39,000 signatures coming from the Vatican alone, a tiny city with a population of a mere 800. In an effort to educate the readers of my blog and offer a means to promote a healthy discussion, I'll today discuss the mechanisms of chain hacking and how they affect systems around the world.
Simply put, botnets are a network of remotely controlled computers called bots. These computers are each affected by a specific type of malware, which allows them to be remotely controlled as a network by a hacker. Not all botnets are malicious, of course, but generally speaking, we only use the term to refer to the malicious ones. Computers controlled remotely via a botnet can be used for a variety of unsavory tactics, including stealing information, infecting and disrupting devices and even spying on users via a webcam.
A botnet always includes a multitude of computers all working together in the interests of a hacker under the influence of a malware. The said malware could be a virus designed to disrupt devices, a spyware designed to look for potential information or even a keylogger looking for passwords and the like. All of this can potentially damage the security of a larger network of computers, which could belong to an office, an organization, a network of organizations or even the government itself.
There are several ways to be affected by a botnet. Visiting a website, downloading a torrent, opening an email, plugging in an infected pen drive or simply connecting to an unsafe network, this can all lead to a connected attack that can affect hundreds, or even thousands of devices integrated into a network. Of course, such a large scale attack is of great concern to larger organizations, which is exactly why such extended measures to prevent them.
The first thing that hackers look for in order to infiltrate a network is a vulnerability, which is pretty easy to find unless one takes the required measures. Safeguarding your network with a proper internet security and anti malware software helps protect it against trained botnet attacks. Using free DNS hosting services can be yet another potential vulnerability and must be plugged, as mentioned by Redstor.com in its recent article on botnet attacks. Keeping your operating system up-to-date is yet another necessity. Ultimately, of course, protecting your data by arranging for a safe external backup machinery such as a cloud is an unbeatable idea.
The threat against security on the internet is on the rise. As every single organization and individual tries to influence the world wide web in its own way, conflict is a must, and we must simply see to where this conflict leads.