Is it the biggest breach in U.S. history?
For almost a month, the Office of Personnel Management (OPM) has been engaged in damage control after publicly disclosing that it was the victim of a massive data breach of government employee data. When first announced in early June, it was believed that the illegally accessed data was limited to basic employee information like Social Security numbers, birthdates, etc. -- now it appears to have included the far more sensitive SF-86 forms as well.
While many Americans may be wondering what the big deal is (after all more people were affected by the Target, Home Depot and JP Morgan breaches), the reality is that this is one of, if not the, most significant breaches of classified government employee information ever uncovered.
Here are eight things everyone should know:
Why is this government security breach so important?
Because the OPM is the human resources department for all of the federal government's civilian agencies, it is the central repository for all personnel files, background checks and other sensitive information on US government employees.
This type of personnel information is extremely valuable to foreign intelligence services, which are likely to use it to blackmail, bribe or recruit US government workers for espionage purposes as well as hack these employees using personal information to trick them into downloading files or clicking on links. They may also use it to figure out who some of our intelligence assets are overseas. To put this in perspective, this breach could end up causing as much long-term damage to the US government as Edward Snowden's leak of top-secret NSA documents.
How many people are affected?
The attack was initially thought to have given hackers access to the private information of at least four million current and former government employees at agencies like the Department of Defense. However, new estimates claim as many as 18 million or more government employees may have been affected. Not included in this tally are the family members, friends and foreign contacts of the affected government employees who were also contained in those files.
What is "Einstein" and why did it fail?
"Einstein," which was first deployed in 1995, is a robust, customized intrusion detection system (IDS) that monitors the network gateways of government departments such as OPM for unauthorized traffic. Many businesses rely on commercially available IDS products to help detect a breach quickly after it happens.
The main drawback with Einstein, and other IDS products, is that its effectiveness largely depends on being able to track the "signatures" of known malware and other cyber threats. If an attacker uses custom-made malware, or is sophisticated enough to change the signature of a known virus or Trojan by using methods like compression, encryption or wrapping, the IDS won't be able to detect it.
Think of it this way: IDS is like a bloodhound that's given a scent to look for - mask the scent, and it won't be able to track you. Added to this is another problem: Einstein has been implemented at different rates across federal agencies such as OPM so that protection is not seamless.
What is SF-85 and SF-86?
Standard Form 85 and 86 are required for individuals with sensitive positions in the government that must pass a background check. Think of it as when you may have filled out a mortgage application, just much more in-depth. These two documents contain extensive information about family members, mental health and credit history. They also include records of "foreign contacts" - lists of non-U.S. officials that a person might know or have relationships with. Such information would be very useful to America's adversaries.
Who is behind this attack?
We'll probably never know with absolute certainty who carried out this attack. Cyber forensics is extremely difficult when you're dealing with a sophisticated adversary, as it's quite easy for hackers to use stolen IP addresses and "onion routers" to mask their true locations and identities. However, it's clear that the data stolen in this attack would most benefit a foreign government - and the evidence released thus far appears to point in the direction of China. For instance, the attackers used similar tools and techniques of a Chinese hacking group called "Deep Panda," which is believed to have hacked Anthem.
How did the attackers gain access?
It's believed the hackers exploited weak authentication systems and that once they had access, they operated as "root" on OPM systems for potentially up to a year or more.
In simple terms, this means they had the keys to the kingdom and operated at the same level as OPM's system administrators. They were able to move terabytes (1 TB is equal to 1,024 gigabytes) of data for months without anyone noticing. According to an internal audit from the end of 2013, only 30 percent of OPM workstations required strong authentication or Common Access Cards (CACs), and none of the agency's 47 major applications required strong authentication.
What's worse, in an audit report published November 12, 2014, auditors found that 11 out of 47 computer systems operated by OPM did not have current security authorizations and that these systems were "amongst the most critical and sensitive applications owned by the agency."
What types of controls did OPM rely on to prevent the breach?
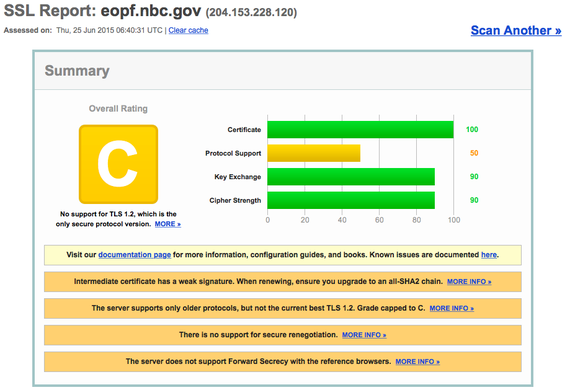
OPM appears to have relied on outdated defensive technologies such as antivirus and other detection systems that can only identify known malware, not advanced persistent threats (APTs). Additionally, a government audit report found seven major systems out of 25 had inadequate documentation of security testing. Even after the breach, security settings on the OPM's website returned a dismal overall grade of "C," and a failing score of 50 on protocol support when checked against one of the leading SSL security checks.
What can be done?
At this point, the cat is out of the bag and all the government can do is try to reduce the damage that will eventually occur because of this massive security breach. We have no idea yet how much this could jeopardize the government's security operations, classified information and foreign intelligence missions.
However, there are a range of things the government can start doing now to prevent future breaches to the OPM and other key agencies. These include: mandating strong encryption, eliminating outdated computer systems, improving patch management, requiring security information and event management (SIEM) technology for 100 percent of federal government and contractor systems, fully implementing NIST 800-171 and deploying APT technologies. A failure to act might lead to a cyber Pearl Harbor.