Now that majority of the internet citizens have dealt with the nasty Heartbleed bug, it's time to take a look at some of the most common security risks that we can experience within our web applications, and perhaps it's time we look into those risks at a much deeper level.
At the end of the day, our customers and employers expect only the best from us; and security issues are not something that you just put aside for later. This year, we saw a huge attack being made on the very popular retail store Target; see here for details - in this attack, 110 million user account details were exposed to hackers.
Last year, Adobe Systems Inc. got attacked by hackers, which lead to an exposure of 3 million user accounts; read the report here - and the year before that, LinkedIn experienced an attack that led to 6.5 million user accounts being exposed to the public.
I don't consider such activity as normal, and although for the average person it only means that he needs to change his password, for many business owners and other money related institutions - it means plenty of headache, sleepless nights, and a lot of security work to be done.
We need to make sure that we're securing our web applications the right way, it's important that developers are aware of the common security pitfalls, and do everything in their power to prevent a new product or an application to be easily exploited, vulnerable.
The Open Web Application Security Project (OWASP) is an open-source web application security project. The OWASP community includes corporations, educational organizations, and individuals from around the world. This community works to create freely-available articles, methodologies, documentation, tools, and technologies.
The OWASP open-source community is hands-down, the absolute best resource for any developer or business owner to go-to whenever there is a need to look into new security issues, or find a way to patch old ones. OWASP offers a handful of solutions, some of which include:
- Security tools and ethics
- Security books on variety of topics
- Security libraries and controls
- State of the art research
- Provides conferences all across the globe
- Mailing list access for latest updates
Hackers, criminals, or whatever is the word we may choose to give people who exploit vulnerabilities, they've got access to a wide variety of ways of manipulating your infrastructure, more specifically - your web applications.
It's important to know that there isn't just one way of attacking a web application, but multiple ways that have their own scale of difficulty and threat level, some are less serious; while others need to be avoided at all costs.
A tiny mistake can go a very long way, and in the worst case scenario, it may even put an end to your company - which would be unfortunate, giving that we've got access to all this material on how to protect ourselves and our customers.
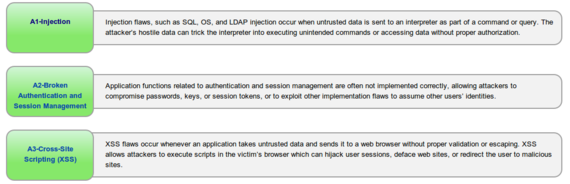
10 Web Application Security Risks
Last year, OWASP foundation published a list of the top 10 most serious web application security threats, and it's the most detailed review of these flaws that you will find anywhere else on the web.
You can find that list by following this link, make sure that you've got time on your hands - as there is plenty of research and new information to learn about.
It will all make more sense when you begin to investigate your own code, and start implementing the much needed precautions as provided by the OWASP foundation website. It's more serious that we think, and in the most recent news - a security company from Sweden, had gained read access to one of Google's production servers; a feat that many hackers dream about.
They were rewarded a $10,000 bounty, and plenty of media attention to last them for a lifetime. Are you serious about the security of your web applications, and what steps have you taken to prevent such attacks from happening?